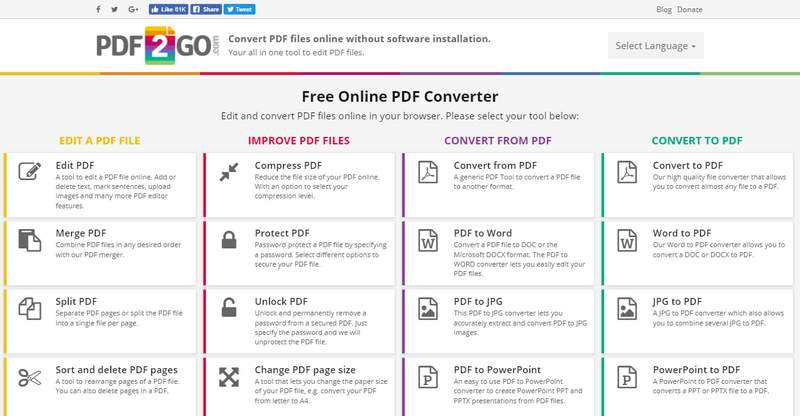
Online Tools You Can Use In Splitting PDF Files
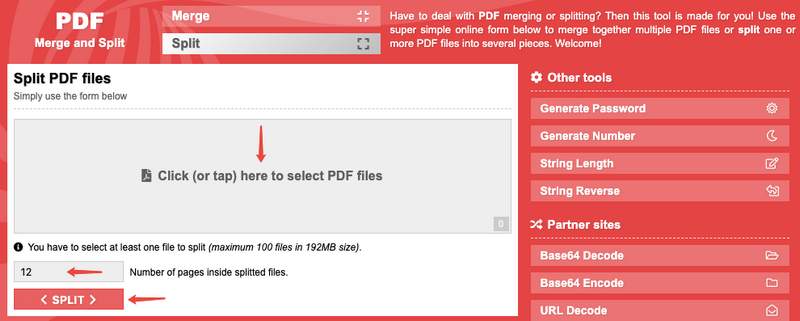
The problem that we encounter with PDF files is that sometimes, the PDF file is too large. Because of that, we are unable to send them through email, and that we need to reduce its size. Another problem is that sometimes, it’s a hassle to read everything in the PDF file to look for whatever is necessary. There are many ways to reduce the size of your PDF files, such as splitting, reducing, compressing, and more. The splitting PDF files help users select which pages they want and what they find necessary to save in a separate PDF file. It will also help reduce the size of the document. Nowadays, so many sites on the internet are provided where we can use online tools for free in the browser or download them to our desktop or mobile devices. The following are the most popular sites for online tools and more to split your PDF files: