
Microcontrollers are widely used in nowadays electronic and modern devices. You can track them whether for personal use for fun or even for serious and confidential applications by banks, security services, government authority, or the military field. Most of the algorithm that uploaded into its memory is well written in Assembler.
Many villains out there want to hack or attack the microcontroller, maybe just for fun or for their own purposes (some of them willing to hack and sell the top-secret from companies for profitable) To reduce the risk of being attack by these microcontroller hackers, that is why we must know the types of attack categories.
Those four major attack categories that involve microcontrollers are:
Microprobing
This method is an invasive attack, which once been used it can directly access the chip surface. Then, we can observe, reprogram and interfere with the integrated circuit.
Eavesdropping
It can easily eavesdrop on the monitor with high time resolution and other electromagnetic radiation by the processor during regular operation.
Fault Generation
It will use the abnormal environment situation to produce malfunctions in the processor and dominate the integrated circuit.
Software Attack
Use the processor’s standard communication interface to penetrate and exploit the security in the protocols or manipulate the algorithm.
The latter three methods are non-invasive attacks and the most dangerous and vulnerable compare with the invasive attacks. First of all, even the secret keys of the comprised card had been stolen, but the owner still didn’t notice it, which could expose their system to great danger. Secondly, it is easy to get the equipment to crack the system, as the cost and tools needed for non-invasive are mostly cheap.
Invasive Attack on Microcontrollers
Most of us think that this invasive attack is much more complicated than a non-invasive attack. Do you believe that we just a few simple tools, we can easily break the PIC12C508A device? (You do not need any particular or high tech device, like the Doctor Who’s Sonic Screwdriver to broke the PIC12C508A device)
Well, let us get started…
- First, you need to use the fuming nitric acid to remove plastic above the chip die (The fuming nitric acid will not harm the chip and bonding wires).

- After it, remove the acid with acetone and clean the sample in an ultrasonic bath.
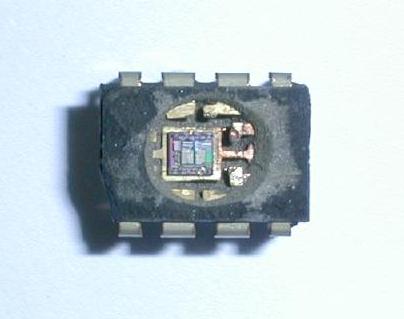
- Then, do wash the chip to remove the salt and dry it up.

- After the chip had dry, you need to further to the next stage, which exposes the protection fuses to the UV light. Remember to find the chip first and protect them from damage.
- You can use opaque paper to protect the program memory from UV light.
- You can read the program memory with any programmer units after exposing the chip under UV light for five to ten minutes.
Non-Invasive Attack on Microcontrollers
This method considered a lot easier than the invasive attack, in which we can penetrate and dominate the chip with simple and cheap software. Ok, let’s take this PIC16F84 as a sample.

The above PIC16F84 is operating IBM PC under MS-DOS or Windows 95/98, and it was written in C++. With just a simple hardware controller, we can continuously change the power supply and programming voltages.
In conclusion, we must remember one thing; every microcontroller has its own way of being hack and attack; that’s why we must always schedule a daily or weekly system checkup. This will reduce the chance of being a hack and ensure that the system performance is standing on a top-notch. [Source]

